Hi, what do you want to do?
Other
Gilc: Cryptography and Liberty
This site from the Global Internet Liberty Campaign reports on a 1998 survey conducted by the Electronic Privacy Information Center which asked world nations about their encryption policies. The survey got results from over 75 nations,...
National Institute of Standards and Technology (NIST)
Fipsp: Authentication Technology Alternatives
These guidelines describes the primary alternative methods for verifying the identities of computer system users, and provides recommendations toFederal agencies and departments for the acquisition and use of technology which supports...
Khan Academy
Khan Academy: Public Key Encryption
Public Key Encryption, an asymmetric encryption technique, is used to allow computers to securely communicate. The high level process is explained in this article.
Khan Academy
Khan Academy: Symmetric Encryption Techniques
Symmetric encryption techniques are explained including the Vigenere Cipher and AES-128.
Other
Um: The Battle Over Cryptographic Key "Escrow"
This article describes the legal and technical issues involved in cryptography. It also discusses government proposals concerning the clipper chip.
Get Safe Online
Get Safe Online: Businesses
A comprehensive guide to protecting your business in today's digital world.
Texas Instruments
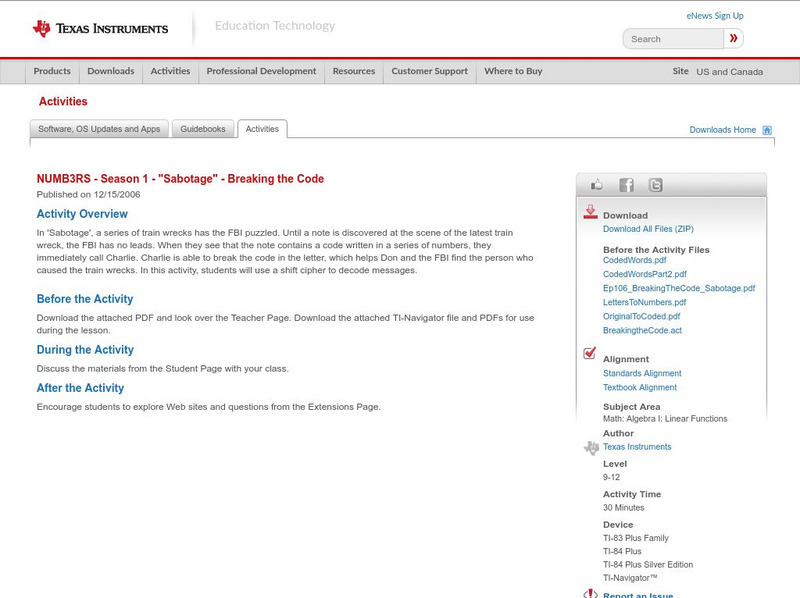
Texas Instruments: Numb3 Rs: Breaking the Code
Based off of the hit television show NUMB3RS, this lesson introduced students to simple coding techniques (namely, the shift cipher). Students learn to translate codes from nonsense to English by quantifying each letter, and then...
American Rhetoric
American Rhetoric: Arthur W. Coviello: Rsa Conference Keynote Address
This is the text and video of Arthur W. Coviello's keynote speech at the RSA Conference delivered on February 25, 2014, in San Francisco, California.
American Rhetoric
American Rhetoric: Ashton Carter: Drell Lecture on Innovation and Cybersecurity
This is the text, audio, and video [40:52] of Secretary of Defense Ashton Carter's Drell Lecture on innovation and cybersecurity delivered on April 23, 2015, at Stanford University, in Palo Alto, California.
Khan Academy
Khan Academy: Congruence Relation
A quick comprehension check over congruence relation.
Khan Academy
Khan Academy: Modular Multiplication
Practice problems over modular multiplication in cryptography.
Khan Academy
Khan Academy: Modular Addition
Practice problems for reviewing modular addition in cryptography.
Other
Global Internet Liberty Campaign: Regardless of Frontiers
"Protecting the Human Right to Freedom of Expression on the Global Internet" is the resource's topic. Lists the Global Internet Liberty Campaign's principles for promoting human rights and civil liberties. Introduction and overview...